Understanding the skill level of your team is essential when designing InfoSec training experiences.
InfoSec training programs don't consider the skill level of their audience. If training is too easy or too hard, your team members won't adopt crucial security behaviors. This could have serious consequences for the security of your organization.
Take an example from your own experience: Chances are, you've been in and out of your comfort zone throughout your life. There have probably been many times when you undertook tasks that were not challenging, keeping you in your comfort zone and allowing boredom to inevitably set in. But too much of a challenge, and you'd have likely been forced into the 'panic' zone, which stalls progress.
What's generally needed is a happy medium: a goldilocks zone, if you will. If you think about it, you'll have encountered learning in the goldilocks zone in your own past. For example in first or second grade, before you were able to read. Sure, you knew the alphabet but you weren't yet able to read or write words. But with the help of your teacher, you slowly learned how to read and write short phrases like “eat apple”, “boy runs”, or “cat on the mat”. Without guidance, reading on your own would've been far too difficult.
We've found that conventional InfoSec training programs struggle to find the goldilocks zone. They don’t provide levels of guidance that are just right. And yet considering the skill level of your audience is important when activating new security behaviors.
One way to find this balance is by leveraging the Zone of Proximal Development (ZPD). Harnessing the power of the ZPD creates an environment where learning feels rewarding and easy. In this article, we'll show you how we use this concept in our learning experiences to give you some food for thought when designing or choosing your training programs.
What is the ZPD?
The ZPD is the distance between what a learner can do without help, and what they can do with support from someone with more knowledge or expertise. Russian psychologist, Lev Vygotsky, developed the concept in the early 1900s.
You can imagine the ZPD as a moving target. Experts guide learners through tasks slightly above their skill level in a process known as scaffolding. The one-on-one interaction with an expert helps learners to make connections between concepts and how to apply them in everyday life. The goal of scaffolding is not to give learners the answers, but to create a structure for building their own knowledge. This makes learning more efficient and effective.
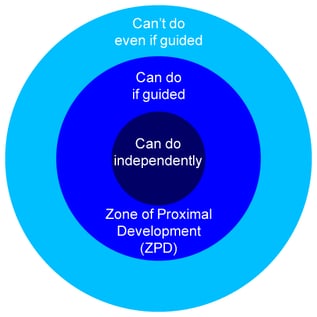
The more competent a learner becomes, the less guidance they need. For example, when you were learning how to read, your ZPD was your ability to read and write short words; and the teacher who helped you to grasp them (using pictures and other methods) provided the scaffolding.
Although scaffolding is used primarily in early childhood education, the ZPD is applicable anywhere an individual has the opportunity to develop new skills – such as in cybersecurity training.
How to create scaffolding in your cybersecurity training
Identify what a learner already knows
By identifying a learner's prior knowledge, you can build on that skill set when introducing new concepts. Before starting a training program, create a list of questions to show your team members' security maturity score to see where they are in their ZPD.
Ask meaningful questions
During a learning experience, ask learners what they think. The right question at the right time can unlock learning. Questions can direct learners’ attention, allowing them to connect the dots between new ideas and old ones. The right questions can also open new spaces in learners' minds, enabling them to form new neural pathways.
Some examples of questions to ask in your InfoSec training are:
- What else could you do here?
- When you do this, what happens?
- What do you notice?
- What was your thought process here?
- How could you apply this in your work?
- Why do you think that happened?
Connect prior knowledge to new ideas
One of the most effective ways to scaffold learners is by linking old and new knowledge. Incorporate this into your InfoSec training by posing a question that requires learners to analyze a scenario.
For example, let's use network security as the topic: get your team to rename their home Wi-Fi network and then change the password. When completed, ask your team two questions:
- What is your top tip for remembering to change your passwords?
- How does regularly changing passwords improve your online safety?
Asking learners to contribute will enable them to become active in the learning process, draw on their experiences, and incorporate what they've learned.
Peer learning
Peer learning is powerful when leveraging the ZPD in your learning programs. Vygotsky maintained that learning occurs through purposeful, meaningful interactions with others.
Some learners may grasp a concept right away, while others are still in their ZPD. Working together allows people to learn both from and with each other while providing the space to practice new tasks supported by peers.
Incorporating peer learning into your cybersecurity training initiatives can be easier than you think. For example, get your team to read some content or watch a video on a particular cybersecurity topic and then discuss the material with a colleague. Or get team members with a high-security maturity score to share their insights and practices with other team members at lower levels of security maturity.
Final Thoughts
To sum up: behavioral activation happens within the ZPD. Actions that can be done independently are unchallenging and dull. Actions beyond the ZPD are exhausting and stressful. Only within the ZPD do people find an action effortful and meaningfully rewarding.
Understanding how to leverage the ZPD prepares you to create learning experiences that are effective and tailored to the needs of your team.
Are you ready for training that incorporates the ZPD and its related concepts? Read more about our 21-day Security Maturity Quest and how it can improve security maturity by up to 25%.